Database security, particularly for MySQL systems, holds critical importance due to the increased incidence of cyber threats. MySQL’s widespread application across diverse scales of operations attracts substantial cybersecurity risks, including data breaches. The escalation in digital data heightens these risks, impacting data integrity and financial resources. This article provides a guide for beginners on strengthening MySQL database security. The focus will be on key strategies and best practices for cybersecurity in MySQL databases, addressing vulnerabilities in the current digital context.
Common MySQL Security Threats
Understanding the security threats that MySQL databases face is crucial for implementing effective protection measures. Here are some of the most common security concerns that database administrators and users need to be aware of:
Mismanagement of Account Access
Proper account management is vital in database security. Mismanagement, such as granting excessive permissions to users or neglecting to remove access for former employees, can lead to unauthorized data access and manipulation.
Weak Passwords
The use of weak or default passwords is a common vulnerability. Attackers can easily exploit these to gain unauthorized access to databases, leading to data theft or corruption.
DDoS Attacks
Distributed Denial of Service (DDoS) attacks can overwhelm MySQL servers, rendering them unable to process legitimate requests. This can cause significant downtime and disrupt access to crucial data.
SQL Injection Attacks
SQL injection is a technique used by attackers to execute malicious SQL statements. This exploits vulnerabilities in the application’s software and can lead to unauthorized access, data theft, and database corruption.
Privilege Escalation
This involves exploiting vulnerabilities in the database system to gain elevated permissions beyond what a user or process is initially granted. Such escalation can lead to unauthorized data access or system control.
Insecure Connections
Data transmitted over unsecured connections can be intercepted and tampered with. Ensuring that connections to the MySQL database are encrypted and secure is essential to protect data in transit.a
Unpatched Vulnerabilities
Like all software, MySQL can have vulnerabilities. Failing to apply patches and updates promptly leaves databases exposed to known risks that attackers can exploit.
Remote Preauth User Enumeration
This threat involves attackers remotely identifying user accounts in a MySQL database without authentication. Knowledge of valid user names can facilitate further attacks, such as brute-force password attacks.
To effectively shield a MySQL database from these threats, it’s crucial to adopt a comprehensive and proactive approach to cybersecurity, focusing on strong access controls, regular updates, vigilant monitoring, and employing best practices in database management and security.
Making MySQL Secure Against Attackers
Securing a MySQL database requires a multifaceted approach, addressing various vulnerabilities to safeguard against potential attacks. Here are some key strategies to enhance MySQL security:
Enforcing Strong Passwords and Removing Default Accounts
One of the first lines of defense in database security is to ensure that all user accounts have strong, complex passwords. It’s also crucial to remove or secure default accounts that come with the initial MySQL installation, as these can be easy targets for attackers. Regularly updating passwords and using password management tools can further bolster security.
Unix User Privileges and Secure File Management
When MySQL runs on a Unix-like system, the security of the database is closely tied to the security of the underlying operating system. It’s essential to run MySQL under a dedicated user account with limited privileges. This containment strategy ensures that even if the MySQL server is compromised, the attacker’s ability to access other system areas remains restricted. Additionally, secure file management practices, like restricting access to critical MySQL files and directories, are vital.
Restricting the FILE Privilege
The FILE privilege in MySQL allows users to read and write files on the server hosting the database. This can be a significant security risk if misused. Limiting or revoking this privilege for users who do not require it can prevent unauthorized data exportation or manipulation of server files.
Encrypting Logs
MySQL server logs can contain sensitive information, including user queries and system messages. Encrypting these logs ensures that even if they are accessed unauthorizedly, the information they contain remains protected and unreadable. Implementing encryption not only secures the logs but also aids in compliance with data protection regulations.
By rigorously applying these security measures, administrators can significantly reduce the risk of attacks on MySQL databases. Regularly reviewing and updating security protocols in line with evolving threats and best practices is equally important in maintaining a robust defense against attackers.
Implementing Security Measures and Best Practices
Securing MySQL databases in today’s digital era requires vigilant implementation of robust security measures and adherence to best practices. This section focuses on two crucial aspects: MySQL Security Configuration and MySQL Security Best Practices. We will delve into optimizing MySQL settings to strengthen database defenses, encompassing various configuration strategies critical for security enhancement. Additionally, we’ll explore a range of recommended practices, essential for database administrators and users. These include regular monitoring, auditing, and employing the principle of least privilege. This comprehensive guide aims to fortify your MySQL database against the escalating threats in the digital domain.
MySQL Security Configuration
Effective MySQL security configuration is pivotal in protecting databases from unauthorized access and potential threats. Here are some key areas to focus on:
User Access Control: The foundation of MySQL security is robust user access control. It’s crucial to meticulously manage user permissions and roles. Implement strategies like creating individual user accounts for each person who needs database access, assigning privileges based on the principle of least privilege, and regularly reviewing and updating these permissions. Also, consider using tools like MySQL’s GRANT and REVOKE statements for precise control over what each user can do within the database.
Encrypted Connections: To safeguard data in transit, MySQL should be configured to use encrypted connections. This prevents data from being intercepted and read by unauthorized parties. Utilize MySQL’s support for SSL/TLS encryption to secure data as it moves between the server and clients. Configuring encrypted connections involves generating SSL certificates and keys, and then configuring MySQL to use these cryptographic tools. This ensures that sensitive information, such as user credentials and the data being queried, remains secure from eavesdropping.
Auditing and Logging: Implementing a comprehensive auditing and logging mechanism is essential for tracking and analyzing activities within your MySQL database. Audit logs can help in identifying unauthorized access attempts, understanding user activities, and providing insights into potential security vulnerabilities. MySQL’s audit plugins can be configured to log a variety of activities, including login attempts, query execution, and changes made to the database schema or data. Regularly reviewing these logs helps in early detection of suspicious activities and aids in compliance with various data protection regulations.
Properly configuring these aspects of MySQL not only strengthens the security of your database but also provides a framework for ongoing monitoring and response to potential security incidents. It’s a proactive step towards ensuring the integrity and confidentiality of your data in the MySQL database.
MySQL Security Best Practices
Adopting best practices in MySQL security is critical to safeguarding databases from potential vulnerabilities and attacks. Here are some key practices to enhance the security of your MySQL installations:
Removing Default Settings and Restricting Remote Access
One of the initial steps in securing a MySQL database is to remove or modify default settings that may be exploitable. This includes changing default port numbers and removing any default accounts that come with the MySQL installation, especially those with well-known usernames and no passwords. Additionally, restricting remote access to the database server is crucial. If remote connections are not necessary for your environment, disable them. If remote access is required, ensure it’s tightly controlled and limited to specific, trusted IP addresses or networks. Implementing firewalls or VPNs can also add an extra layer of security.
Regular Security Assessments
Continuous security assessments are vital for maintaining the security of your MySQL database. This involves regularly scanning for vulnerabilities, reviewing user privileges, and ensuring that the database is up to date with the latest security patches and updates. Tools like MySQL Workbench can be used for routine maintenance tasks, including checking for updates and managing user accounts. Regular security audits help in identifying potential vulnerabilities before they can be exploited.
Strong Authentication Credentials
Strong authentication mechanisms are essential to prevent unauthorized access. Use complex passwords for all database accounts and consider implementing additional authentication methods such as two-factor authentication (2FA) for enhanced security. Encourage or enforce password policies that require users to create strong, unique passwords and change them periodically. Also, consider using authentication plugins provided by MySQL for more advanced authentication options.
By adhering to these best practices, you can significantly reduce the risk of security breaches and ensure that your MySQL databases remain secure and robust against evolving cyber threats. Remember, a proactive and vigilant approach to security is key in protecting sensitive data stored in your MySQL databases.
Ensuring Secure Connections and Replication
dbForge Studio for MySQL is a comprehensive GUI tool designed to enhance MySQL database management, development, and administration. It offers an array of features including data comparison, synchronization, and an intuitive interface for efficient database operations. A crucial aspect of this tool is its emphasis on security, particularly in establishing secure connections and replication processes.
For secure connections, dbForge Studio facilitates SSL/TLS setup, ensuring encrypted network traffic and protecting remote user configurations. While specific steps for securing replication traffic and verifying server certificates were not directly available, the general approach involves using SSL/TLS for data transmission, thus safeguarding the data replicated between servers and verifying server certificates to prevent unauthorized access. This comprehensive approach to security is essential in maintaining the integrity and confidentiality of data in MySQL databases.
SSL/TLS for Network Traffic and Remote User Configuration
dbForge Studio for MySQL allows setting up SSL/TLS encrypted connections to enhance security. This is achieved by opening the Database Connection Properties dialog, switching to the Security tab, and selecting ‘Use SSL’. You will need to specify the location of the client key, client certificate, and authority certificate. This setup ensures that the data transmitted over the network is encrypted, protecting it from interception and unauthorized access.
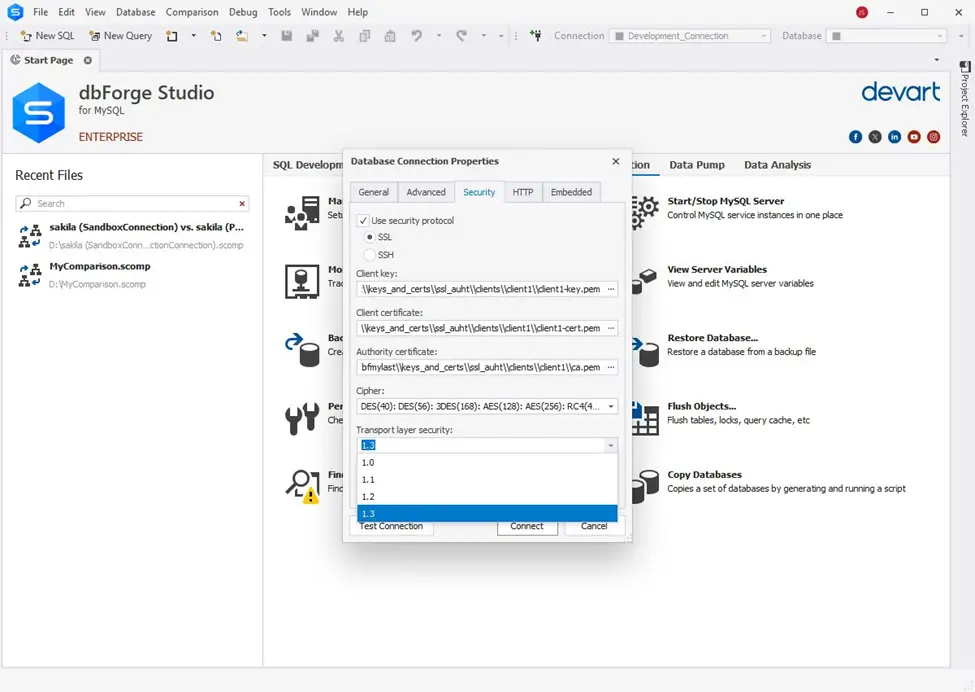
Securing Replication Traffic and Verifying Server Certificates
While specific documentation on securing replication traffic and verifying server certificates using dbForge Studio for MySQL wasn’t directly found, the general principle involves ensuring that the data replicated between servers is transmitted over secure channels, such as SSL/TLS encrypted connections. This includes setting up SSL certificates for both the source and destination servers and configuring the replication process to use these secure connections. Additionally, verifying server certificates as part of the SSL/TLS setup is crucial to prevent man-in-the-middle attacks and ensure that the servers are communicating with the legitimate source and destination.
Implementing these security measures in dbForge Studio for MySQL is essential for maintaining the integrity and confidentiality of the data being managed and replicated.
Conclusion
Securing a MySQL database involves crucial steps like enforcing strong user access controls, establishing encrypted connections, and implementing rigorous auditing and logging. Tools like dbForge Studio for MySQL play a vital role in simplifying these processes through their user-friendly interfaces and robust feature sets. This journey to secure MySQL databases demands constant vigilance and adaptation to evolving cyber threats. As such, database administrators and users are encouraged to maintain ongoing security awareness, regularly update their practices, and utilize advanced tools to ensure the protection and integrity of their database assets in an increasingly digital world.

